Iranian Gov Hackers, intercept 2FA via SMS to access activist accounts
Iranian government hackers in the recent months, repeatedly managed to hack activists / journalist email and social media accounts protected by Two Factor Authentication. The first major incident reported in the media was Imam Ali charity in Iran, although this was not the first by any means. here are their Tweets (in Persian), informing Gmail, Telegram, LinkedIn, and Facebook accounts of a large number of their colleagues in the organization has been hacked:
اطلاعیه شماره ۲
حمله سایبری سازمان دهی شده از طریق پیامکهای مخابرات
در صبح روز پنجشنبه ۶ اردیبهشت ۹۷، حمله سایبری به اکانتهای تلگرام، جیمیل، فیسبوک و لینکدین تعداد زیادی از اعضای جمعیت امام علی شکل گرفت.— جمعیت امام علی (@imamalisociety) April 26, 2018
And in late September, a lawyer has tweeted the same attacks on her Gmail and Telegram accounts, and also many other woman's rights activists in Iran:
امروز صبح(ساعت 6.30) حساب تلگرام و حیمیل من هک شد( به رغم دو مرحلهای بودن)
تلگرامم رو از نو ساختم و همین الان ایمیلم رو پس گرفتم. کدوم نهاد و مرجع و با چه مجوزی ساعت 6.30 به اطلاعات شخصی من دست پیدا کرده؟
پ.ن: تلاش برای هک عدهای از فعالین زنان امروز گسترده بوده، #اطلاعرسانی https://t.co/xQ1ANlZOBC— samin cheraghi (@samincheraghi) September 26, 2018
How this possibly happens:
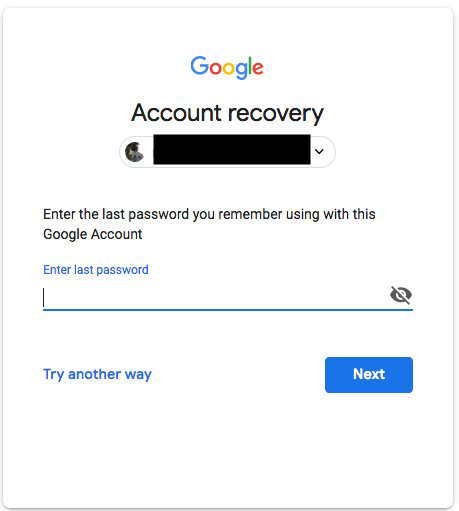
What happens is Iranian security forces have successfully phished or otherwise gained access to a target's Gmail password. Then they send a 2FA request, usually in very early mornings when target is sleep, using the victim's phone number. As they have full access to the country's mobile operator networks, they intercept the 6 digit code sent by Google:
- Hacker choose Password Recovery
- Hacker sees OTP, and clicks on "try another way"
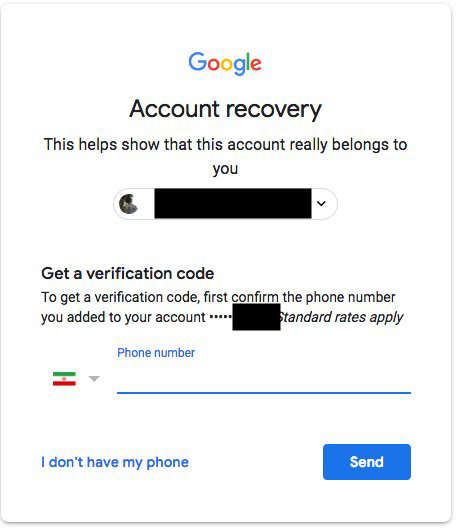
- Hacker enters the mobile number of the Victim and request a code via SMS
- Hacker enters the victim's mobile number, intercept the SMS on operator, and enter the 6 digit code to gain access to the account
Once they have access to the email of the victim, they start resetting passwords of their social media accounts, i.e. Twitter, Facebook, Linkedin, etc.
Using the same technique, for instant messengers:
As most instant messenger Apps, i.e. Telegram, Whatsapp and others use SMS to authenticate their users, once attacker can intercept the victims SMS, they can simply authenticate a new session for their instant messengers and read their messages. Very few IMs like Telegram, actually offer a second factor for authentication - in case of telegram, a password - but many do not have this function activated, as it is not required by the platform.
Workarounds:
Iranian users are advised to use offline methods only, i.e TOTP for their second factor authentication, and delete their phone numbers from their google records so it can not be used for password recovery or 2FA fallback. As for the instant messengers, they should activate the 2FA for the platforms that support this, and quit the ones they don't support 2FA.